General
In the General tab you decide how log entries will be saved.
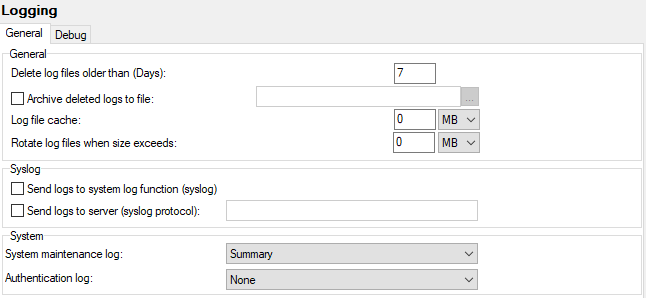
Figure. Logging management: General tab.
General section
Log files are saved into the <install_dir>/logs directory (if not changed within the System > Storage > Directories tab) or a subdirectory thereof:
Saved in <install_dir>/logs directory with a file name of axyyyymmdd-nn.log, where:
So, m120190913-01.log is the first server second IMAP log for 13th September 2018.
Subdirectories are named according to the logging data contained therein, they are:
-
activesync
-
Antispam
-
antivirus
-
ldap
-
loganalyzer
-
maintenance (settings changes, e.g.: 'System' updated '123@icewarpdemo.com')
-
purple
-
reports (for spam / quarantine reports)
-
setup (installer logs)
-
sip
-
syncml
-
syncpush
-
voip
-
webdav
-
webmail
Note: There is the setup.log file within the <install_dir>/logs/setup folder. This file is valid only for Windows installations. For information on Linux setup, refer to the Installation and Control in Linux.pdf guide.

